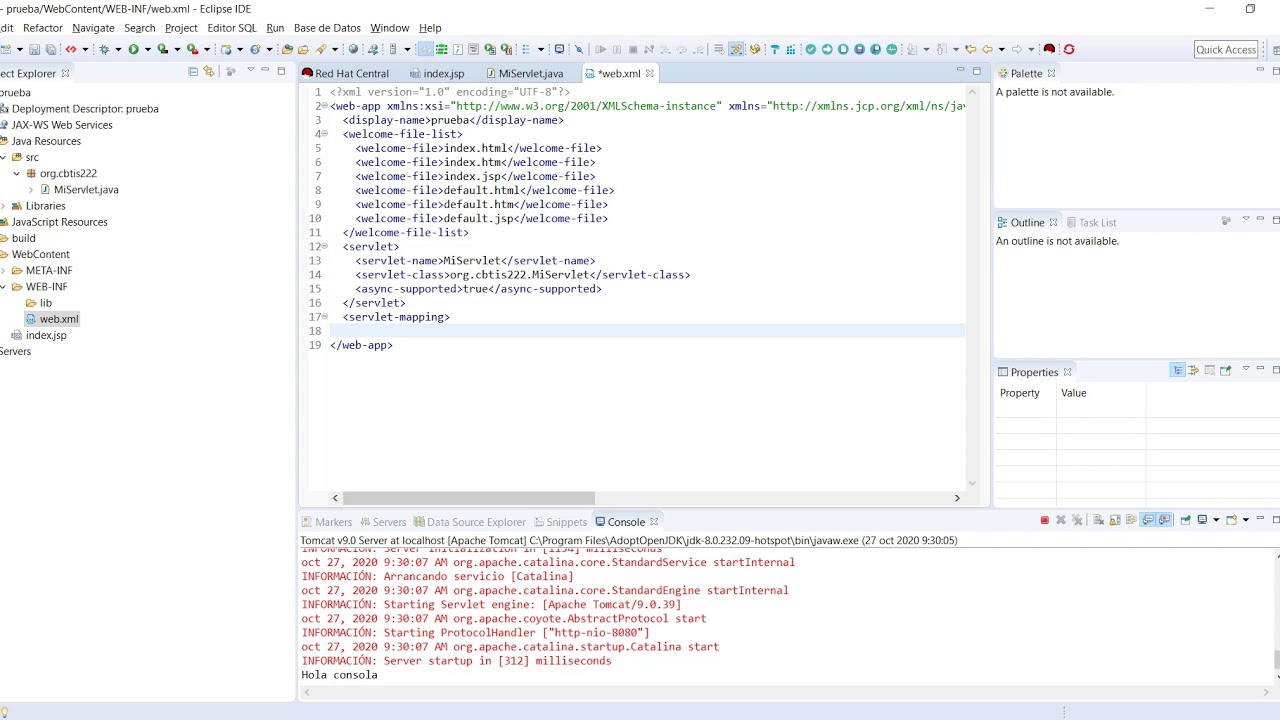
How to add security constraint in web xml?
Specifically, you use the @HttpConstraint and, optionally, the @HttpMethodConstraint annotations within the @ServletSecurity annotation to specify a security constraint. If your web application does not use a servlet, however, you must specify a security-constraint element in the deployment descriptor file.
- Q. What is user data constraint?
- Q. Is Web XML mandatory for JSP?
- Q. What is security role in web xml?
- Q. What is URL pattern in web xml?
- Q. Why is security a constraint?
- Q. When should I use WEB xml?
- Q. What is WEB xml file in servlet?
- Q. What is Web XML and its purpose?
- Q. Is security a role?
- Q. What is a servlet URL?
- Q. What is URL pattern servlet?
- Q. What are security constraints in web.xml use cases?
- Q. Why is web.xml not getting applied to url?
- Q. What do security constraints mean in web container?
- Q. How to define a security role in web.xml?
Q. What is user data constraint?
A user data constraint can be used to require that a protected transport layer connection such as HTTPS (HTTP over SSL) be used for all constrained URL patterns and HTTP methods specified in the security constraint. The user data constraint is handy to use in conjunction with basic and form-based user authentication.
Q. Is Web XML mandatory for JSP?
No, there will be no need of web. xml for servlet based application if you are using servlet version >3.0 and tomcat 7 as it will not run in the previous versions of tomcat. Annotation represents the metadata.
Q. What is security role in web xml?
xml. A role can be mapped to specific principals, specific groups, or both. The principal or group names must be valid principals or groups in the current default realm. The role-name element must match the role-name in the security-role element of the corresponding application deployment descriptor (web.
Q. What is URL pattern in web xml?
The url-pattern element of a servlet-mapping or a filter-mapping associates a filter or servlet with a set of URLs. When a request arrives, the container uses a simple procedure for matching the URL in the request with a url-pattern in the web. xml file. A URL pattern may contain a subset of US-ASCII characters.
Q. Why is security a constraint?
A security constraint is used to define the access privileges to a collection of resources using their URL mapping. If your web application does not use a servlet, however, you must specify a security-constraint element in the deployment descriptor file.
Q. When should I use WEB xml?
Java web applications use a deployment descriptor file to determine how URLs map to servlets, which URLs require authentication, and other information. This file is named web. xml , and resides in the app’s WAR under the WEB-INF/ directory.
Q. What is WEB xml file in servlet?
The web. xml file is located in the WEB-INF directory of your Web application. The first entry, under the root servlet element in web. xml, defines a name for the servlet and specifies the compiled class that executes the servlet. xml, under the servlet-mapping element, defines the URL pattern that calls this servlet.
Q. What is Web XML and its purpose?
web. xml defines mappings between URL paths and the servlets that handle requests with those paths. The web server uses this configuration to identify the servlet to handle a given request and call the class method that corresponds to the request method.
Q. Is security a role?
A security role is a collection of project-level privileges that are assigned to users and groups. A group is a collection of users that can be assigned privileges (or security roles) all at once, for the project source and all projects in it. A security role is a collection of privileges in a project.
Q. What is a servlet URL?
Servlet mapping specifies the web container of which java servlet should be invoked for a url given by client. It maps url patterns to servlets. When there is a request from a client, servlet container decides to which application it should forward to. Then context path of url is matched for mapping servlets.
Q. What is URL pattern servlet?
The url-pattern element of a servlet-mapping or a filter-mapping associates a filter or servlet with a set of URLs. When a request arrives, the container uses a simple procedure for matching the URL in the request with a url-pattern in the web. xml file.
Q. What are security constraints in web.xml use cases?
Security Constraints consist of Web Resource Collections (URL patterns, HTTP methods), Authorization Constraint (role names) and User Data Constraints (whether the web request needs to be received over a protected transport such as TLS). In this section, we will look at specifying the security constraints for multiple use cases.
Q. Why is web.xml not getting applied to url?
For example, if you have /test/list/user.xml, then this will be treated as a web resource collection in Super user Area and thus SUPER_USER can only have access. so, ensure that url-pattern is declared more specific to resources to avoid clashes and mis-interpretation. Thanks
Q. What do security constraints mean in web container?
Security Constraints. It is important to realize that any combination that was intended to be secure but was not specified via security constraints, will mean that the web container will allow those requests. Security Constraints consist of Web Resource Collections (URL patterns, HTTP methods), Authorization Constraint (role names)…
Q. How to define a security role in web.xml?
Define roles with the security-role. Then map these roles to principals in your realm with the security-role-assignment . In web.xml, define which resources in the Web Application the security constraint applies to by using the element that is nested inside the element.
Paso número 3. Configuración del archivo web.xml
No Comments