How do I configure the device for better security?
10 Tips to Securely Configure Your New Devices
- Q. What is a secure configuration?
- Q. What is the most secure network security?
- Q. How can I make my Android more secure?
- Q. How do you configure a device?
- Q. How do you secure a smart home?
- Q. How do you manage system configuration?
- Q. What is a configuration standard?
- Q. Which is more secure AES or TKIP?
- Q. What is the best security mode for WiFi?
- Q. Which Android phone is most secure?
- Q. Can someone watch you through your phone?
- Q. What are the requirements for Secure Device Configuration?
- Q. Which is the best router security option should you choose?
- Q. Which is the minimum security configuration for an enterprise?
- Q. What are the most common security misconfigurations?
- Adjust Factory-Default Configurations on Hardware and Change Default Passwords.
- Secure your Wi-Fi Network with Encryption.
- Double Your Login Protection.
- Disable Location Services and Remote Connectivity.
- Safeguard Against Eavesdropping.
- Don’t Broadcast Your Wi-Fi Network Name.
Q. What is a secure configuration?
Secure configuration refers to security measures that are implemented when building and installing computers and network devices in order to reduce unnecessary cyber vulnerabilities. Security misconfigurations are one of the most common gaps that criminal hackers look to exploit.
Q. What is the most secure network security?
WPA3 (Wi-Fi Protected Access version 3) is the latest security protocol with top standards. WPA3 protects against dictionary attacks and uses Simultaneous Authentication of Equals handshake, which protects its network from attacks that could be possible with WPA2 in place.
Q. How can I make my Android more secure?
Strengthening Android security
- Use phone locks.
- Use a VPN.
- Use two-factor authentication.
- Download apps only from the Google Play Store.
- Use anti-virus software.
- Do not use WiFi and Bluetooth connections at an unknown place.
- Enable Android’s “Find My Device” feature.
- Browse in safe mode.
Q. How do you configure a device?
Step 2: Set up the new device
- Turn on a new device that isn’t set up yet. Put the device in pairing mode.
- Turn on your phone’s screen.
- On your phone, you’ll get a notification offering to set up the new device.
- Tap the notification.
- Follow the onscreen steps.
Q. How do you secure a smart home?
12 tips to make your smart home more secure
- Give your router a name.
- Use a strong encryption method for Wi-Fi.
- Set up a guest network.
- Change default usernames and passwords.
- Use strong, unique passwords for Wi-Fi networks and device accounts.
- Check the setting for your devices.
- Disable features you may not need.
Q. How do you manage system configuration?
The Manage System Configuration screen allows you to download, save, switch, revert and delete system configuration files. To Manage System Configuration, navigate to Configuration > System > Maintenance > Manage Config on the Web UI, advanced mode. The table below lists the available system configuration files.
Q. What is a configuration standard?
Configuration Standard: A document or collection of documents that describe how a device should be configured. Standards are the specifications that contain measurable, mandatory rules to be applied to a process, technology, and/or action in support of a policy.
Q. Which is more secure AES or TKIP?
TKIP is no longer considered secure, and is now deprecated. In other words, you shouldn’t be using it. AES is a more secure encryption protocol introduced with WPA2. AES isn’t some creaky standard developed specifically for Wi-Fi networks, either.
Q. What is the best security mode for WiFi?
WPA2-AES
The bottom line: when configuring a router, the best security option is WPA2-AES. Avoid TKIP, WPA and WEP. WPA2-AES also gives you more resistance to a KRACK attack. After selecting WPA2, older routers would then ask if you wanted AES or TKIP.
Q. Which Android phone is most secure?
Most secure Android phone 2021
- Best overall: Google Pixel 5.
- Best alternative: Samsung Galaxy S21.
- Best Android one: Nokia 8.3 5G Android 10.
- Best cheap flagship: Samsung Galaxy S20 FE.
- Best value: Google Pixel 4a.
- Best low cost: Nokia 5.3 Android 10.
Q. Can someone watch you through your phone?
Regardless of whether you use an Android or an iPhone, it is possible for someone to install spyware onto your phone that will secretly report on your activity. It’s even possible for them to monitor your cell phone’s activity without ever even touching it.
Q. What are the requirements for Secure Device Configuration?
The recommendations below are provided as optional guidance to assist with achieving requirement 3.1, Secure Device Configuration. Resource Custodians must utilize well-managed security configurations for hardware, software, and operating systems based on an industry standard.
Q. Which is the best router security option should you choose?
Ultimately, AES is more secure. So, Which Router Security Option Should You Choose? Here is a list of the security protocols ranked from the most secure to least secure: WPA2 and AES are the best settings to secure your Wi-Fi connection from hackers.
Q. Which is the minimum security configuration for an enterprise?
Enterprise basic security – We recommend this configuration as the minimum-security configuration for an enterprise device. Recommendations for this security configuration level are generally straightforward and are designed to be deployable within 30 days.
Q. What are the most common security misconfigurations?
Some of the most common security misconfigurations include incomplete configurations that were intended to be temporary, insecure default configurations that have never been modified, and poor assumptions about the connectivity requirements and network behavior for the application.
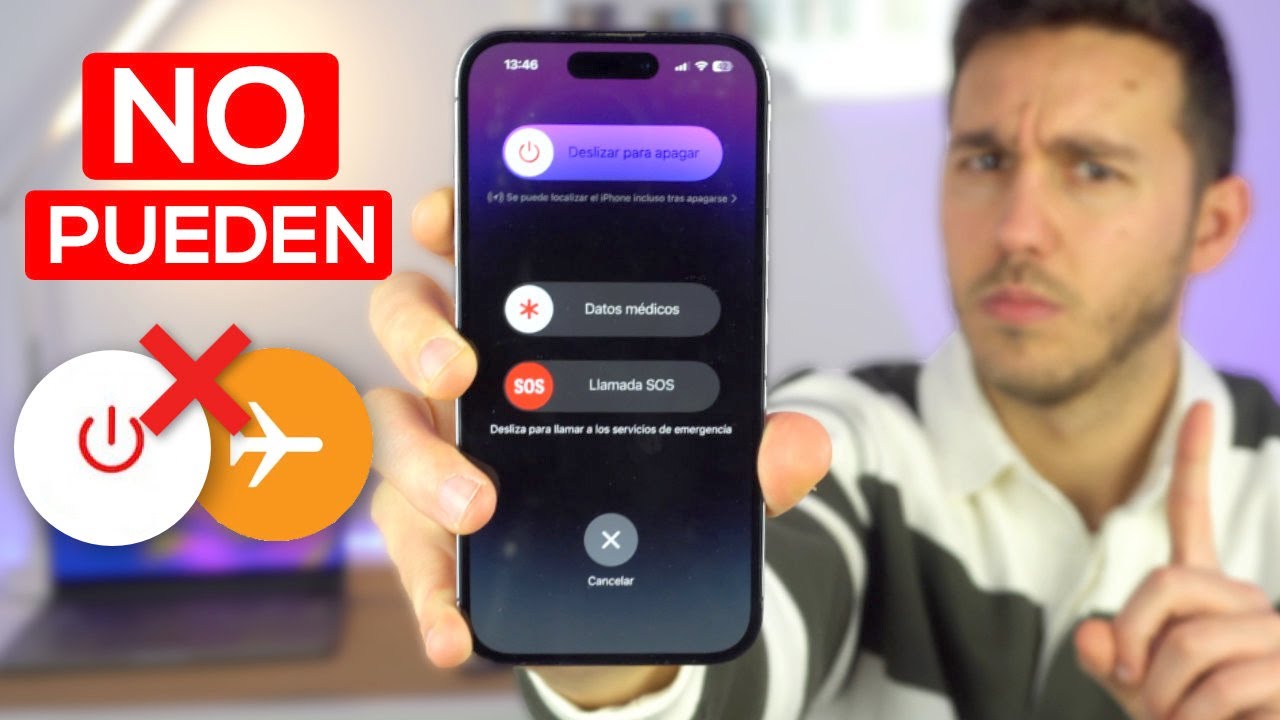
Te ayudo a como evitar que apaguen tu iPhone y a crear un dispositivo antirrobo, esta es la forma de proteger tu iPhone de robos que es algo muy importante p…
No Comments